The Power of Blind Consensus: How UMA's Commit-Reveal Prevents Collusion
TLDR: UMA Prevents Collusion with Commit-Reveal Voting
UMA uses a commit-reveal voting system to secure its decentralized oracle and prevent collusion. By hiding votes during the commit phase, it ensures that voters can’t coordinate or be bribed, creating a truth-telling equilibrium. This design has enabled UMA to resolve over 55,000 outcomes with high accuracy, including major prediction markets, all without relying on centralized trust.
Introduction
What if the best way to find the truth… was to hide it?
That sounds counterintuitive. But in the world of mechanism design and decentralized governance, keeping certain information private can actually improve the accuracy and honesty of a group’s decision-making. When participants are unable to rely on signals from others, they fall back on the one thing they can trust: their own independent interpretation of the facts.
UMA is built around this idea. Its commit-reveal voting process transforms uncertainty into reliability. It’s because of this design that UMA has consistently resolved the truth over 55,000 times, 98.2% of the time without dispute. Even in high-stakes situations like the 2024 Presidential Election prediction on Polymarket, which produced over $3.6 billion in trading volume.
Unfortunately, prediction markets, InfoFi, social media, and many other ecosystems are plagued by manipulation and disinformation. Luckily, UMA offers a model where the right structure produces the right incentives and reliable, trustless consensus.
Let’s break down why hiding votes is so powerful, and how UMA uses blind consensus to turn game theory into truth-finding infrastructure.
The Game Theory of Hidden Votes
The core challenge in decentralized voting is coordination. How do you get a group of people to independently vote for the right answer without letting them influence or be influenced by one another? Without a central authority to guide decisions, decentralized networks must rely on emergent consensus, which is fragile in the face of visibility and influence.
This is where Schelling points come in. First introduced by Thomas Schelling, these are outcomes that people naturally converge on without communicating with each other. In prediction markets or oracle systems, the truth itself is often the most obvious Schelling point, but only if voters can’t see each other’s answers beforehand. The moment transparency is introduced into the voting process, voters may be incentivized to coordinate, game, or free-ride on others' insights.
When Seeing Votes Breaks the System
There have been several real-world cases where transparent voting backfired:
Steem vs. TRON (2020): TRON founder Justin Sun teamed up with exchanges like Binance and Huobi to use customer funds to vote out Steem’s validators in a hostile takeover. Transparent voting allowed them to time the move precisely. The community responded by forking the chain to launch Hive. (Source)
Compound Proposal #289 (2024): A whale named “Humpy” and allies bought COMP tokens to push through a $24M treasury proposal benefiting their own product. Visible vote tallies let them know exactly how many tokens they needed. (Source)
EOS Vote Buying (2018–2020): Leaked documents showed exchanges like Huobi colluding to vote each other into top validator slots. EOS’s fully transparent DPoS system made mutual vote-buying easy to coordinate, and even monetize. (Source)
Curve Gauge Wars: Curve’s visible gauge voting spawned a bribe economy, where protocols pay users to direct liquidity rewards their way. Platforms like bribe.crv.finance only work because onchain voting is publicly verifiable. (Source)
MakerDAO Coalitions: Research shows that large MKR holders often form coalitions and dominate governance outcomes. Because voting is fully transparent, these groups can track each other’s behavior and coordinate off-chain to secure proposals. (Source)
In each case, visibility didn't improve accuracy. It introduced incentives to coordinate, free-ride, or manipulate. They key takeaway here? If votes are visible, coordination becomes manipulation.
How Hiding Votes Leads to Honest Outcomes
On the other hand, Hidden votes create a separation between intention and execution. This way voters are incentivized to report truthfully because they can’t predict or be bribed by others’ choices. Separation makes individual honesty the optimal strategy.
Vitalik Buterin’s essay on Engineering Security Through Coordination Problems unpacks this dynamic by showing how systems can intentionally restrict coordination to improve outcomes. He argues that when participants are unable to form “common knowledge”(information that everyone knows everyone else knows), manipulative coordination becomes nearly impossible. In UMA’s case, the absence of common knowledge (who voted for what, and when) removes the possibility of preemptive collusion. Voters are left in an information vacuum, but one that paradoxically produces greater truth. Although it may seem limiting, this information vacuum forces each voter to rely solely on their own signal, resulting in a more truthful aggregate outcome.
That’s why UMA’s commit-reveal voting process matters so much. It makes sure that no one knows how others are voting until it’s too late to adjust. The result? A system where honesty is encouraged and mathematically optimal.
How UMA’s Commit-Reveal Voting Works
UMA’s voting process occurs in UMA’s DVM and operates in two phases:
Commit Phase: Voters submit their vote, which is then hashed and submitted with a secret salt. No one can see how they voted, only that they did vote. This phase lasts 24 hours.
Reveal Phase: After the commit period ends, voters reveal their committed vote and the salt. UMA verifies that the hash matches the reveal. Once this happens, voters can see the results, which include the number of unique addresses that voted, the total tokens committed, the distribution of votes, and the final resolution. This phase also lasts 24 hours.

This system is simple but powerful. It ensures:
Independent voting: Voters cannot lazily copy other voters and must do their own research.
Front-running prevention: No one can copy or preempt another voter’s answer.
Bribery resistance: Attackers can’t confirm if their bribes worked, so there’s no incentive to bribe.
Anti-collusion: Without verifying other votes, it’s risky to coordinate or vote dishonestly.
Each phase serves a critical purpose. During the commit phase, the hash commitment locks voters into their decisions without revealing them. The reveal phase forces accountability, ensuring that no one can change their answer after seeing outcomes. These two together create an elegant symmetry: secrecy followed by transparency, each at the right moment.
In practice, this means UMA’s oracle creates a game where telling the truth is both virtuous and the safest bet. And in environments where incentives are everything, the safest bet is usually the one that wins.
The Math Behind Honest Voting
UMA’s Data Verification Mechanism (DVM) whitepaper dives deeper into the math behind blind consensus voting. If every voter relies on their own independent (but slightly noisy) signal about the true value, and submits their vote without seeing anyone else’s, something amazing happens. The law of large numbers kicks in, and the collective vote converges on the truth.
But UMA doesn’t just hope for convergence. It enforces it through a reward system that aligns incentives around honest behavior.
Here’s how it works:
If more than 50% of voters agree on a single value (the mode), that value is used as the final resolved price. Only voters who submitted that exact value are rewarded; the rest are penalized.
If no single value passes that 50% threshold, the median is used instead. In that case, only the middle 50% of voters (those who submitted values between the 25th and 75th percentiles) are rewarded. And again, the rest are penalized.
This mechanism encourages accuracy when there’s strong consensus, and moderation when there’s uncertainty. And because commit-reveal ensures votes are hidden during the commit phase, no one can safely game the system. Guessing or coordinating only adds risk. The safest and most profitable strategy? Submit your honest signal.
This setup creates a truth-telling equilibrium. If you’re a rational voter looking to maximize your reward, your best move is to tell the truth.
And this isn’t just theoretical, it’s enforced through economics. The DVM whitepaper formalizes the minimum conditions needed to prevent corruption with a simple inequality:
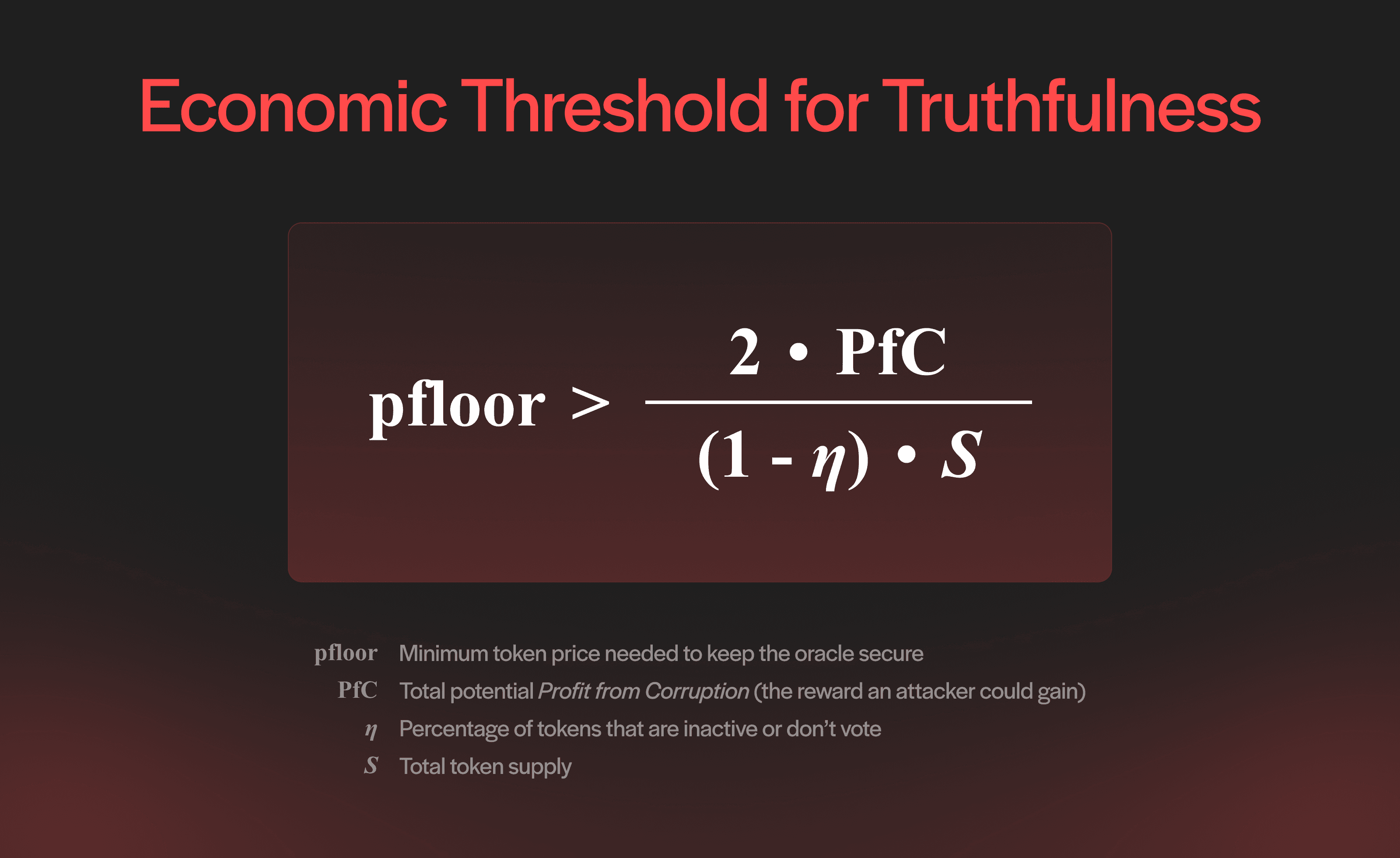
The inequality consists of the following variables:
pfloor is the minimum token price needed to keep the oracle secure.
PfC is the potential Profit from Corruption (the reward an attacker could gain).
η (eta) is the percentage of tokens that are inactive or don’t vote.
S is the total token supply.
As long as the value of the token (pfloor) stays above this threshold, it’s more profitable to vote honestly than to attack. This equation links the protocol’s economic security directly to market value, participation, and design, creating a dynamic where truth isn’t just encouraged; it’s financially enforced.
Truth Without Communication
So what enables UMA’s oracle to consistently reach Shelling points? Three things:
Binary clarity: Many of UMA’s markets are binary (yes/no), which sharpens the focal point and reduces ambiguity.
Shared references: Voters are looking at the same trusted data sources, such as reputable APIs or public datasets.
No common knowledge: Thanks to commit-reveal, there’s no shared info until it’s too late to coordinate. Everyone votes alone.
Even edge cases get resolved through protocol rules: predefined resolutions, quorum thresholds, and fallback dispute rounds ensure fairness. These elements give the system the resilience it needs to handle gray areas, bad-faith actors, or unclear market conditions.
Can UMA Voting Be Exploited? Attack Vectors and Why They Fail
Let’s imagine you're trying to break the system. You’ve got a lot at stake, and you’re willing to stretch the rules (or ignore them entirely) to bend the outcome in your favor. So, how might you try to game UMA’s voting process?
Coordinate secretly with other voters? It’s a gamble. Without knowing how others will vote, or even if they’ll follow through, you’re left vulnerable to defection. You have to trust dishonest actors for the ploy to work, which is a risky move. One honest participant can break the scheme and leave the rest exposed.
Signal dishonestly? Signaling fails when no one can see your vote. Commit-reveal means all signals are locked up until it’s too late to respond.
Bribe voters? Bribes rely on proof. But with commit-reveal, no one can verify how a voter actually voted until after the fact, making bribes unenforceable and economically irrational.
Vitalik Buterin explores this broader dynamic in his essay On Collusion, where he explains how coordination and shared knowledge can undermine mechanism design by enabling strategies that extract value at the system’s expense. He emphasizes that systems should be engineered to limit harmful coordination by removing the incentives and tools that make it enforceable. UMA’s commit-reveal process puts this into practice: by hiding votes until the reveal phase, it removes the visibility and provability that collusive behavior depends on.
When no one can prove or pre-commit to dishonest behavior, collusion becomes too risky to work.
In other words: if manipulation can’t be trusted, it stops working.
Blind Consensus in Action
Claims are one thing, performance is another. Does this system actually work? Absolutely. UMA’s voting protocol isn’t just theoretical. It’s battle-tested, iterated upon, and continuously evolving:
Consistent Success: UMA has resolved the truth over 55,000 times, 98.2% of the time without dispute.
High-stakes votes: Like those resolving markets tied to global events, elections, and volatile financial data.
Edge cases: Where rules are applied consistently even amid ambiguity and emotional controversy.
Real-world cases show this in action. Let’s look at a few examples.
Example 1: Will Kim Moon-Soo Be the People's Power Party Candidate for President?
Political prediction markets have historically driven millions (sometimes billions) of dollars worth of trading volume on Platforms like Polymarket. There was a recent prediction market on Polymarket: Will Kim Moon-soo be the People's Power Party candidate for president?.
The outcome was proposed to UMA’s OO and disputed within the 48-hour challenge window. The dispute escalated to the DVM, where votes were committed and revealed with a final resolution of P2: Yes (meaning that yes, Kim Moon-soo was the People’s Power Party Candidate for President).
This resolution secured $3,582,698 in trading volume within a larger market that experienced over $30 million in trading volume.
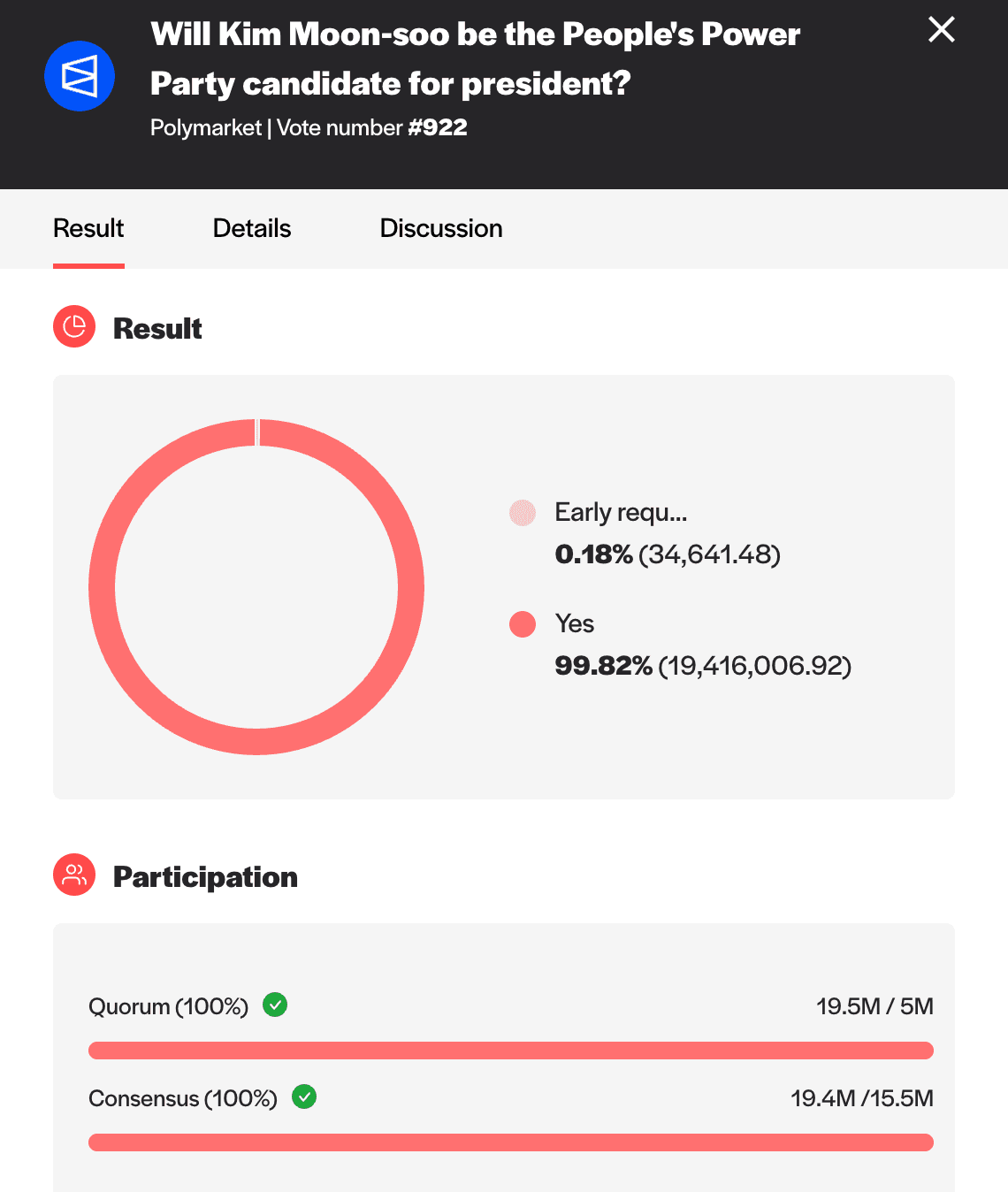
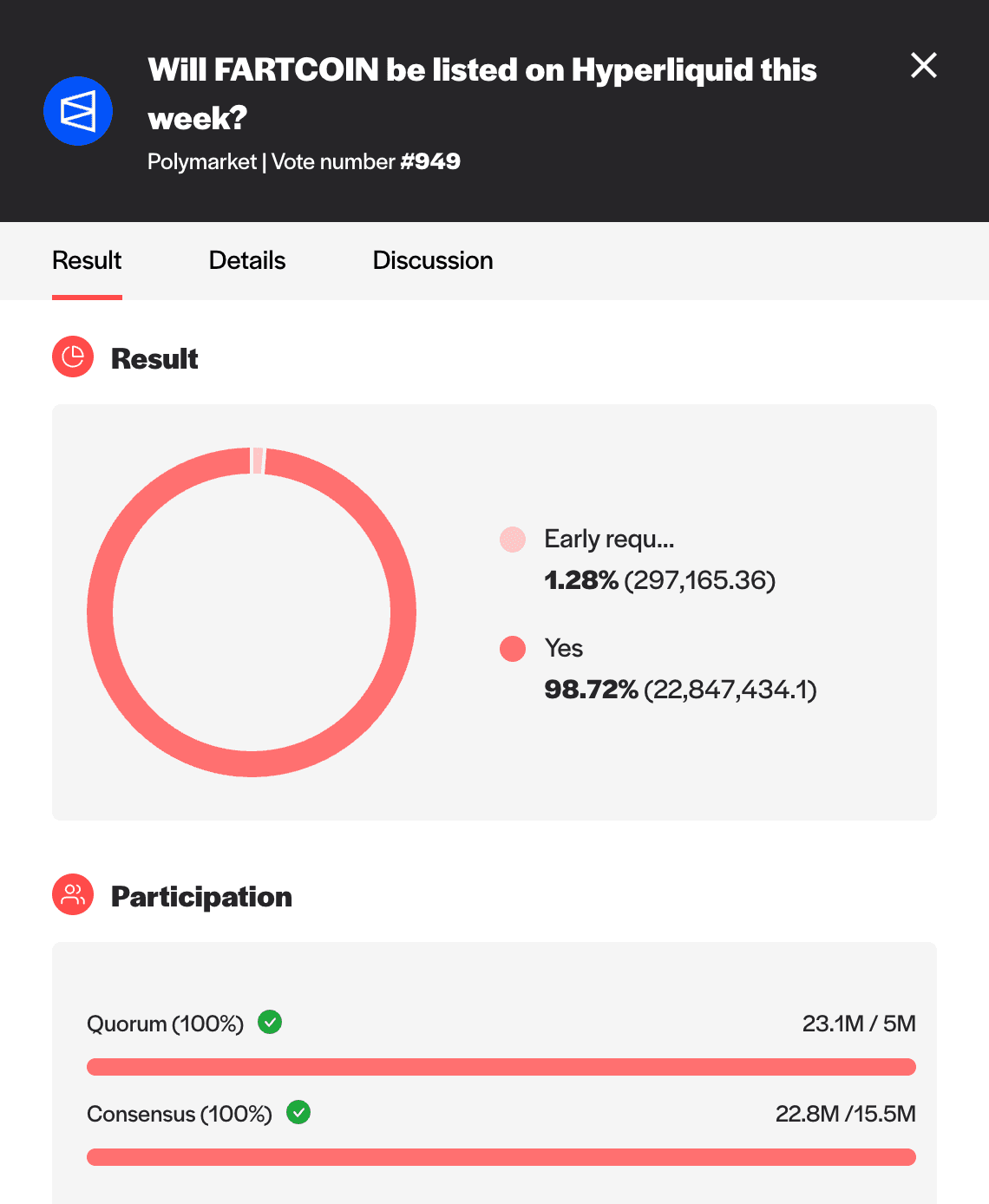
Example 2: Will FARTCOIN Be Listed on Hyperliquid this Week?
Recently, there was a Fartcoin-related prediction market on Polymarket: Will FARTCOIN be listed on Hyperliquid this week?. The market’s rules stated: “This market will resolve to ‘Yes’ if the crypto token Fartcoin ($FARTCOIN) is listed for spot trading on Hyperliquid by May 18, 2025, 23:59 PM ET. Otherwise, this market will resolve to ‘No.’”
The outcome was proposed to UMA’s OO and disputed within the 48-hour challenge window. The dispute escalated to the DVM, where votes were committed and revealed with a final resolution of P2: Yes (meaning that yes, Fartcoin was listed on Hyperliquid within the timeframe stated in the market’s rules).
This resolution secured $738,231 in trading volume.
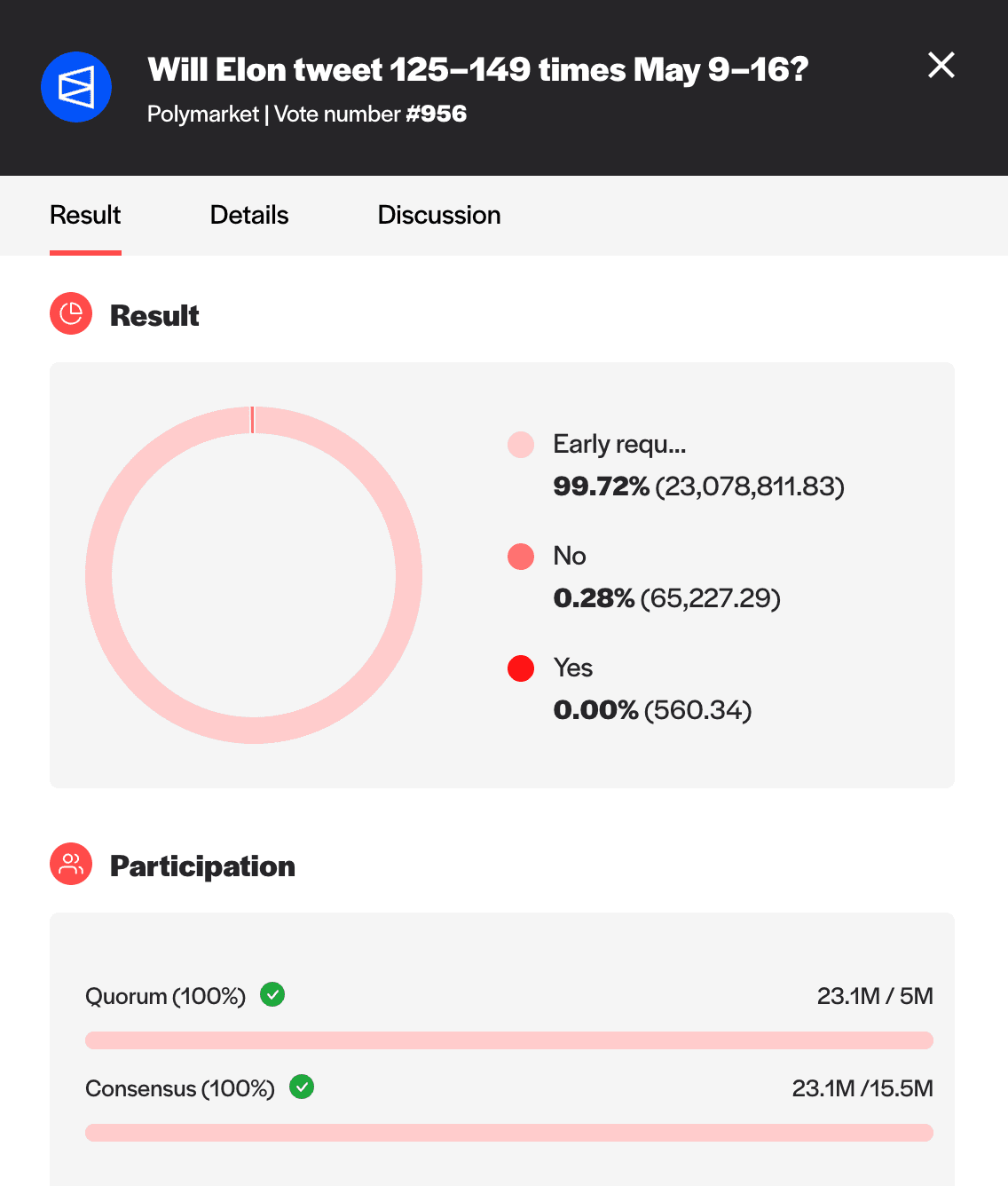
Example 3: Will Elon Tweet 125-149 Times May 9-16?
Finally, let’s look at another recent prediction market on Polymarket: Will Elon tweet 125-149 times May 9-16?.
The outcome was proposed to UMA’s OO and was disputed within the 48-hour challenge window. The dispute escalated to the DVM, where votes were committed and revealed with a final resolution of P4: Too Early (meaning that someone had proposed the answer before the timeframe had concluded).
This resolution secured $189,088 in trading volume within a larger market that experienced over $3 million in trading volume.
In each of these examples, the final results held up to scrutiny, even under the spotlight of millions of dollars and public attention. In the end, voters independently arrived at the Schelling point resulting in a near-unanimous vote.
Learn more about UMA voting here.
Iteration and Improvement
Beyond voting outcomes, UMA’s system generates data on voter behavior, system liveness, and coordination robustness. This meta-data feeds into future upgrades, ensuring that blind consensus becomes not just an event, but an evolving capability.
This isn’t just good design. It’s the foundation for a new era of decentralized truth-finding.
Final Thoughts: The UMA Perspective
In crypto, we often talk about trustlessness. UMA’s commit-reveal system puts that ideal into practice. It shifts trust from people to process, from intention to structure.
By hiding information at the right time, we unlock a deeper truth: when voters act independently, they actually coordinate better. Not by talking, but by trusting the mechanism. It’s a paradox that the best collaboration often comes from isolation, as long as the system is built to reward integrity.
UMA’s blind consensus model doesn’t just prevent collusion. It proves that decentralized communities can find truth together. Not through force or fiat, but through carefully engineered incentives. And in an age of noise, misinformation, and manipulation, that might be the most powerful consensus of all. Because when truth becomes the rational default, everyone wins.
Build with UMA
Want to see how blind consensus can secure your project?
Explore how UMA can support your protocol with reliable, manipulation-resistant data.